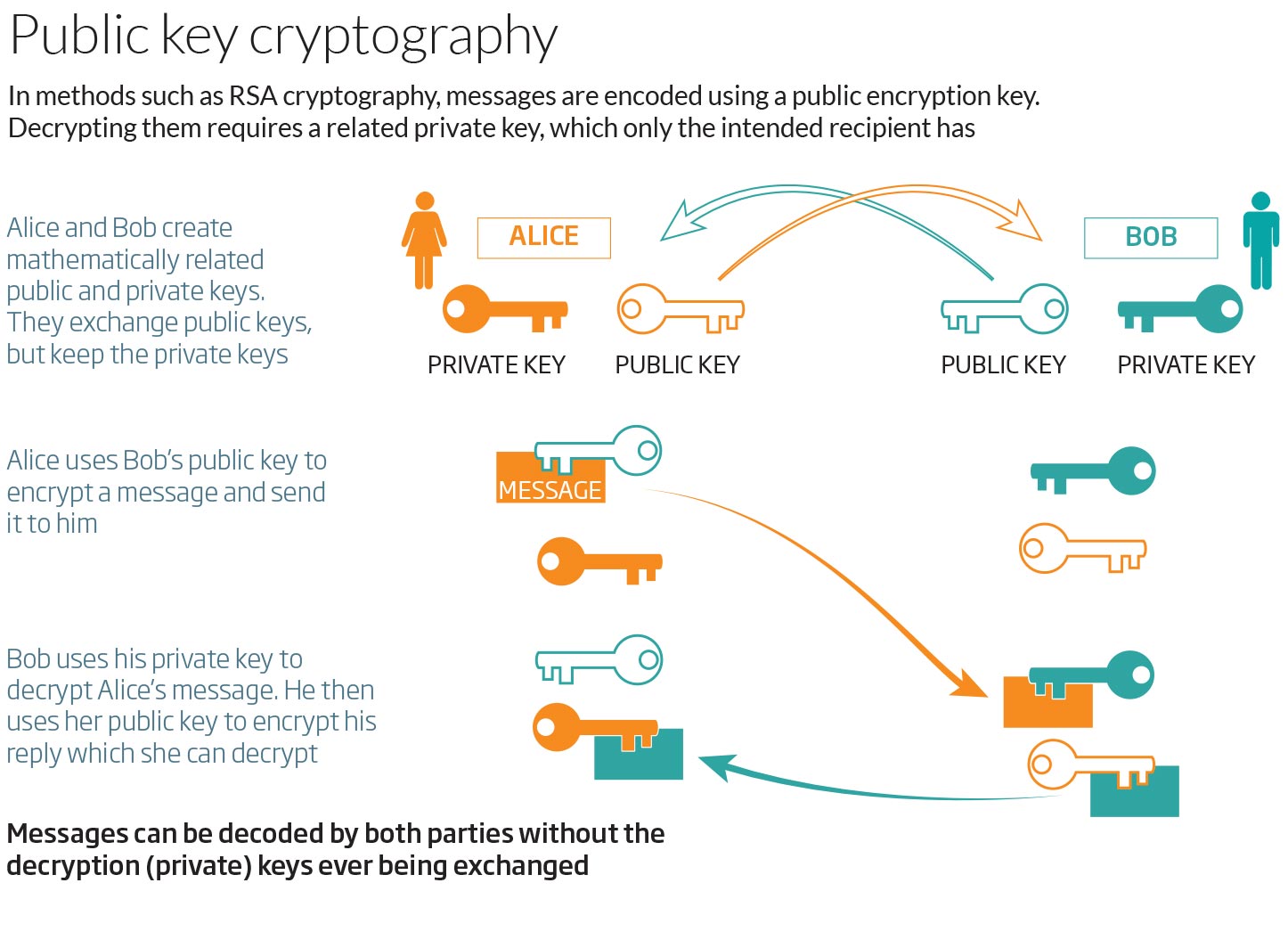
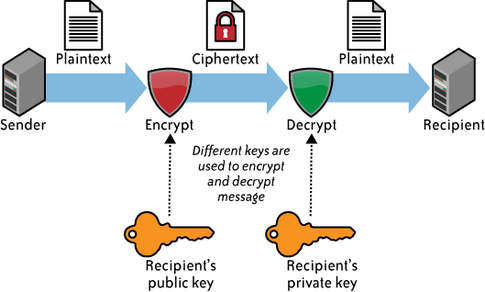
Encryption With Key. Encryption keys are created with algorithms designed to ensure that each key is. Public-key cryptography, or asymmetric cryptography, is a cryptographic system that uses pairs of keys: public keys, which may be disseminated widely, and private keys.

Public Key Encryption - Unlike symmetric key cryptography, we do not find historical use of public-key cryptography.
The working below covers the making of simple keys and the encryption and decryption of a sample of plain text.
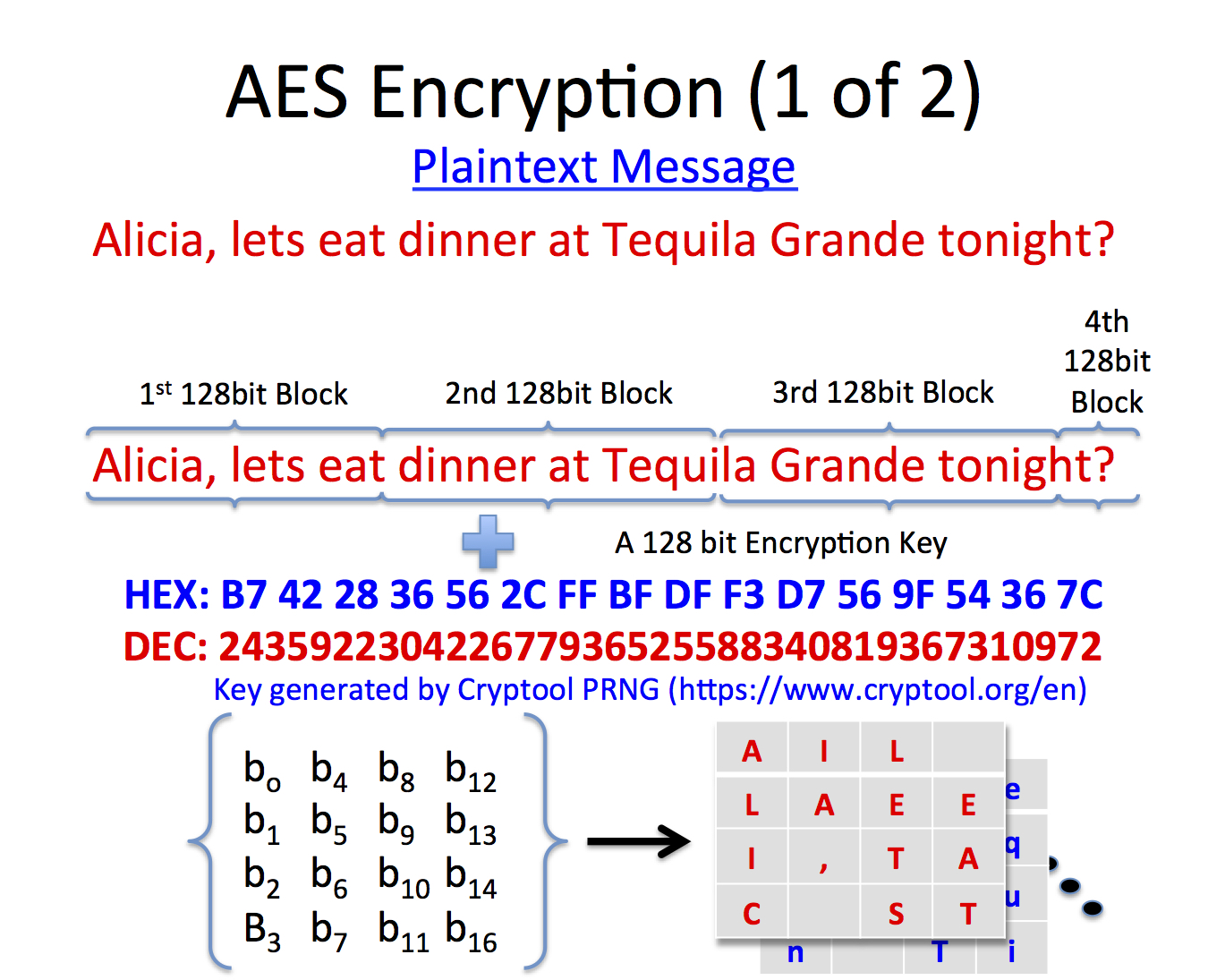
It is computed each time the master password is entered. As the encryption can be done using both the keys, you need to tell the tool. security encryption-key key-management go-application. An encryption key is typically a random string of bits generated specifically to scramble and unscramble data.